Ntlm Domain Name Example
Http Negotiate SPNEGO Negotiate is a scheme which potentially allows any GSS authentication mechanism to be used as a HTTP authentication protocol. If the domain name matches the name of the SAM database the authentication is processed on that computer.
 Asp Net Core Web Api Using Windows Authentication Cors Request Unauthorised Stack Overflow
Asp Net Core Web Api Using Windows Authentication Cors Request Unauthorised Stack Overflow
For example use this group policy to specify that the Active Directory domains AJAXORG and FIREFLYCOM which are outside of the firewall with a one-way trust to the forest inside the firewall use NTLM authentication.

Ntlm domain name example. Add server exceptions for NTLM authentication in this domain policy. All example hashes are taken from Hashcats example hashes page. The client sends a username to the host.
On an Active Directory domain controller the name of the account. In addition the NTLM verifier hash a hash of the NTLM hash is stored to disk to handle offline logons by comparing the password with the cached credentials. Single domain user name.
Use either the group policy Specify NTLM authentication domains or the configuration parameter pamntlmauthdomains. The Wikipedia page on NT Lan Manager has a good. To set this group policy select Computer Configuration Centrify Settings DirectControl Settings Pam Settings Specify NTLM authentication domains.
The domain controllers block all NTLM requests for all domain servers and accounts. Issue is the the Account Name BigDog exists in multiple domains with different. Learn how to establish a SQL database connection using NTLM.
In the second GET request you respond with a server nonce which is the authentication challenge received from the domain controller. This article introduces the steps to test any application that is using NT LAN Manager NTLM version 1 on a Microsoft Windows Server-based domain controller. Deny for domain servers.
Time CC2 domain name v2-Hash HMAC-MD5NT-Hash user name. The host responds with a random number ie. For successful NTLM authentication the MWG needs both the IP address for tcp level communication and the Fully Qualified Domain Name FQDN from here on of the Domain controller for SMB level communication.
7-X64-01 Secure Channel type. 2 minutes to read. Scenario - An application scanning Servers in multiple Domains via their IP Address.
InitializeSecurityContext NTLM returns a token that the client must pass to the remote peer which the peer in turn submits to the local security. If a domain name is not specified as in method 2 and the system property httpauthntlmdomain is defined then the value of this property will be used as the domain name. NTLM is the successor to the authentication protocol in Microsoft LAN Manager LANMAN an older Microsoft product.
Note the important information here - the time user domain transitive logon and originating workstation are all listed. Few may know the trick of adding the Authorization header to prompt a response from the server but I recently discovered NTLM in other protocols that can be exploited using a. The client then generates a hashed password value from this number and the users password and then sends this back as a response.
User Administrator in the Contoso domain used NTLM to connect from his client 7-x64-01 to his server 2008r2-f-04 on Sept 30th at 51321 PM. In a Windows network NT New Technology LAN Manager NTLM is a suite of Microsoft security protocols intended to provide authentication integrity and confidentiality to users. NTLM uses an encrypted challengeresponse protocol to authenticate a user without sending the users password over the wire.
Audit use of NTLMv1 on a Windows Server-based domain controller. The realm portion of this property is optional since the default realm is the same as the realm of the Server. NTLM credentials are based on data obtained during the interactive logon process and consist of a domain name a user name and a one-way hash of the users password.
Turn test case mode on ntlmTEST_CASE True selfuser User selfdomain Domain selfpassword Password selfserverName Server selfworkstationName COMPUTER selfrandomSessionKey bU16 selftime bx008 selfclientChallenge bxaa8 selfserverChallenge bx01x23x45x67x89xabxcdxef selfflags ntlmNTLMSSP_NEGOTIATE_KEY_EXCH ntlmNTLMSSP_NEGOTIATE_56 ntlmNTLMSSP_NEGOTIATE_128 ntlmNTLMSSP_NEGOTIATE_VERSION ntlm. AD Bridge Enterprise stores an NTLM hash and LM hash only for accounts in AD Bridge Enterprise s local provider. Since it is by their IP address Kerberos is not used for authentication.
NTLM authentication does not use a password it uses a challenge-response protocol which requires a few server roundtrips. After you defined the mapping of Active Directory domains to NTLM domains you can specify the list of domains that use NTLM authentication instead of Kerberos authentication. One of the two either IP or FQDN is provided in the MWG configuration.
NTLM uses a challenge-response protocol to check a network users authenticityTo do so the client and host go through several steps. The function is used to build a security context between the client application and a remote peer. The domain name is processed as follows.
PortREALM where fqdn is the fully qualified domain name port is the port number and REALM is the realm of the SQL Server in upper-case letters. Attempting to help a IT Techy colleague out on this issue. It should fall back to NTLM LDAP call to a DC to verify the user account and password.
NTLM authentication requests are forbidden for all servers unless the server name is on the exception list in the Network security. The hashes are used to. For example your SPN.
On a Windows workstation that is a member of a domain the name of the SAM database is considered to be the name of the computer. You have to ensure that the other one can be resolved by. The InitializeSecurityContext NTLM function initiates the client side outbound security context from a credential handle.
The NTLM protocol suite is implemented in a Security Support Provider which combines the LAN.

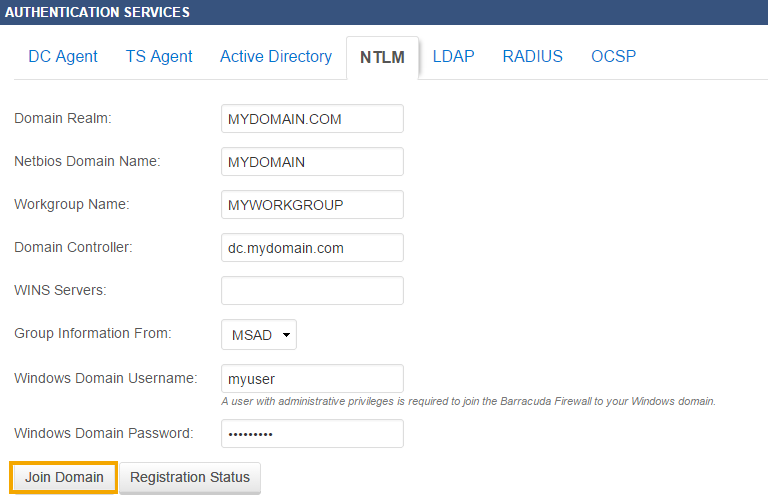 How To Configure Ntlm Authentication Barracuda Campus
How To Configure Ntlm Authentication Barracuda Campus
How To Disable Ntlm Authentication In Windows Domain Windows Os Hub
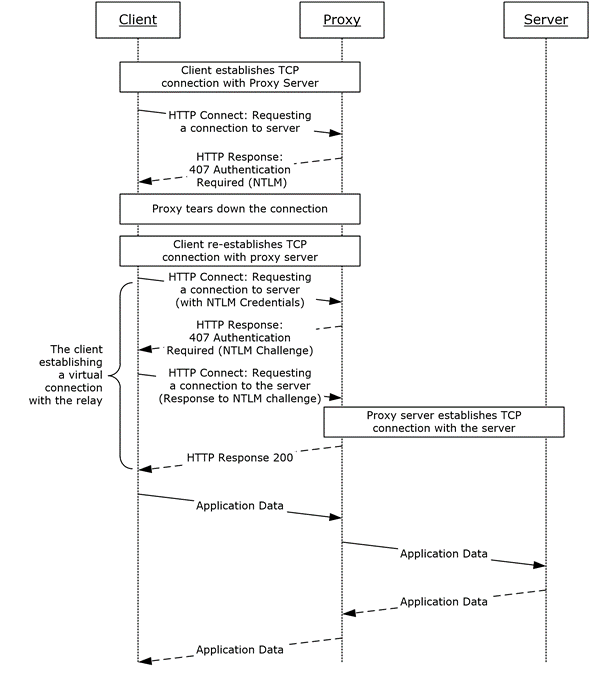 Ms Grvhenc Proxy Authentication Using Ntlm Example Microsoft Docs
Ms Grvhenc Proxy Authentication Using Ntlm Example Microsoft Docs
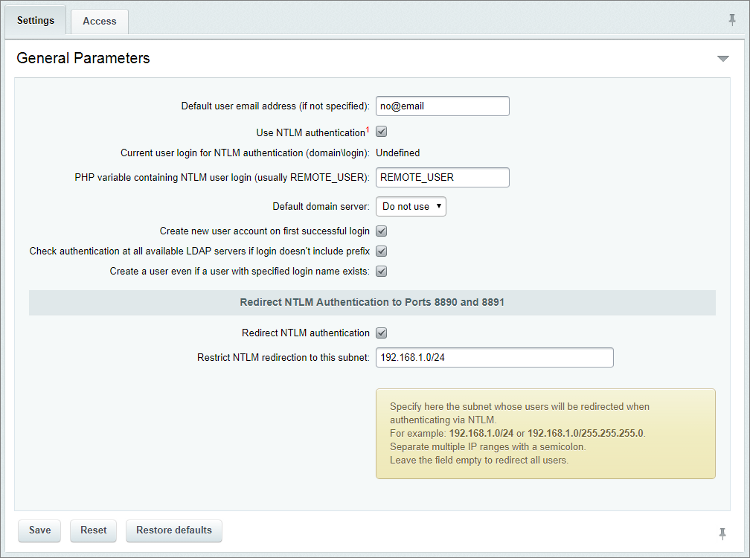 7 Configure Ntlm Authorization For All Sites
7 Configure Ntlm Authorization For All Sites
 Domain Hunter Checks Expired Domains For Categorization Reputation And Archive Org History To Determine Good Candidates For Phishin Computer Security History Names
Domain Hunter Checks Expired Domains For Categorization Reputation And Archive Org History To Determine Good Candidates For Phishin Computer Security History Names

 What Is The Difference Between Negotiate And Ntlm Authentication
What Is The Difference Between Negotiate And Ntlm Authentication
How To Add Header Quot Domain Quot Required By Ntlm In Soap Request
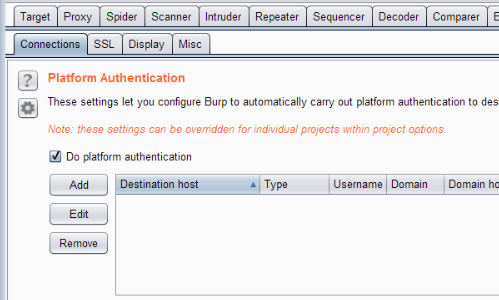 Configuring Ntlm With Burp Suite Portswigger
Configuring Ntlm With Burp Suite Portswigger
 Invoke Psimage Embeds A Powershell Script In The Pixels Of A Png File And Generates A Oneliner To Execute Useful Life Hacks Pixel Script
Invoke Psimage Embeds A Powershell Script In The Pixels Of A Png File And Generates A Oneliner To Execute Useful Life Hacks Pixel Script
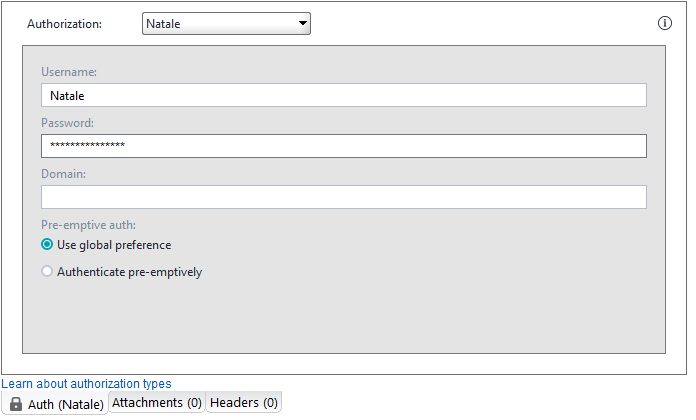 Ntlm Authentication Readyapi Documentation
Ntlm Authentication Readyapi Documentation
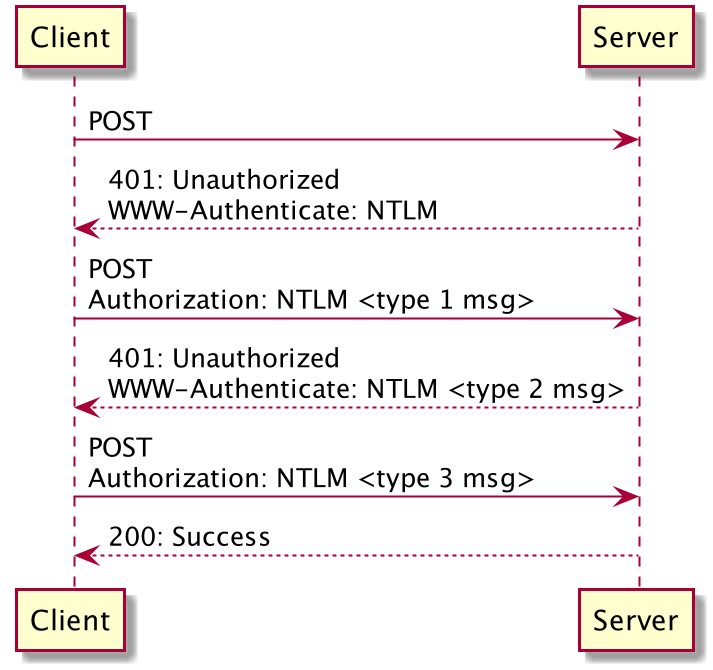 Ntlm Authentication In Java Personal Pastebin
Ntlm Authentication In Java Personal Pastebin
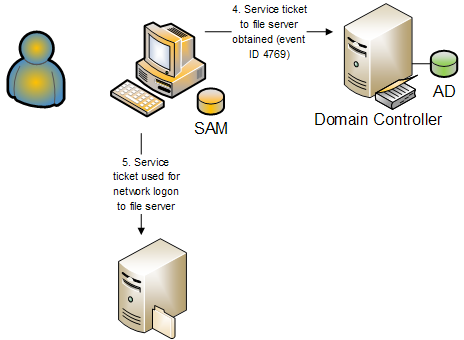 Chapter 4 Account Logon Events
Chapter 4 Account Logon Events
 Microsoft Exchange Zero Day And Exploit Could Allow Anyone To Be An Admin Safe Program Zero Days Edifying
Microsoft Exchange Zero Day And Exploit Could Allow Anyone To Be An Admin Safe Program Zero Days Edifying
 Why Is Ms Sql Server Using Ntlm Authentication Server Fault
Why Is Ms Sql Server Using Ntlm Authentication Server Fault
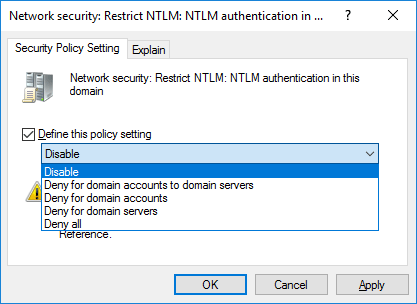 Implement Ntlm Blocking In Windows Server 2016 Rootusers
Implement Ntlm Blocking In Windows Server 2016 Rootusers

Post a Comment for "Ntlm Domain Name Example"